Installation
Starting with version 3.4.0.0 W10Privacy is provided in the form of an installer. This can be used to install the software regularly or, in portable mode, to extract the software as an executable file in any folder (in portable mode, however, the program requires write access in the respective folder!) The program settings of an "installed W10Privacy" are stored in the AppData subfolder "W10Privacy" of the respective user (usually under C:\Users\username\AppData\Roaming\W10Privacy).
Start
W10Privacy is started by a simple double-click. During startup, the program reads in the current settings and
then displays the main window.
At the beginning, the settings of the "Privacy" tab will be displayed. Depending on the settings currently set on the system, checkmarks are placed in front of the various menu items in the grey
boxes (the checkmarks in the grey boxes cannot be changed and serve as a comparison possibility for settings changed later). In the example below, for example, it can be seen that "Disable the
application telemetry" was not active when the program was started, but was then ticked by the user. "Disable asking for feedback" was not set when the program was started and was left as it was
by the user.

If one of the options is unchecked, this naturally means that the respective option is not activated on the system.
Using the Main Window
If an option is to be set, a check mark must first be set or removed (for deactivation). To activate the option via the program, a click on the button "Set changed settings" is necessary.
Options that are preceded by an exclamation mark require administrative permissions, otherwise they cannot be changed.

If you are working on a system without administrative authorizations, the program will not be able to change options that require administrative authorizations.
In this case, the program will display a warning message when attempting to set an option.
In order to make these system-relevant settings anyway, W10Privacy must be executed either directly under an administrative account or, if "only" the user account control is active and one actually has administrative permissions, by right-clicking (--> "Run as administrator") in the administrative context.

Depending on the environment, however, it may happen that when you set the settings in the administrative context, the above note message is also displayed. In such a case, however, this can be
ignored, the settings are still set.
This can be recognized by the status change of the desired option (s) following the setting of the changed settings: After the desired settings have been set, the program re-reads the settings
and displays them in an updated display.

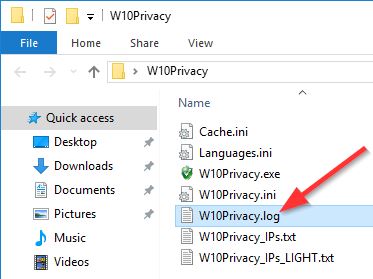
When setting changed settings, W10Privacy creates a log file in the folder where the program is located. The changes made (and attempted) are documented in it. For example,"Attempting" to change the system settings of a normal user will not be successful, but this attempt is documented if necessary.
Using the CommandLine mode
The settings available in the program can also be checked/set via an "unattended command line mode". The idea behind it is that it happened occasionally that
Microsoft has reset one or the other option to its original state in the course of updates... ; -)
In order not to have to start the program manually every day, you can save once set options and start the program - e. g. via task scheduling or an entry in the autostart - in unattended mode. The program then checks the active settings, compares them with those of the saved configuration and adjusts the different settings.
Before saving the configuration, the desired options must be selected in the main window. To save the configuration, select "Configuration" --> "Save".
In the W10Privacy program path a file W10Privacy.ini is created, which contains the selected options.

W10Privacy can then be started in a DOS box via the parameter "/s" and the subsequent parameter "1","2" or "3" in unattended mode.
1 - Check/change all stored settings
2 - Check/change user-specific settings only
3 - Only check/change system-related settings (administrative authorizations required!)
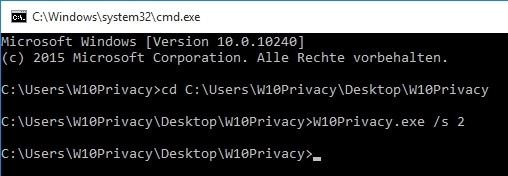
Important: The settings in the "Network" register are not set correctly in the administrative context via the parameter "W10Privacy. exe /s 3", because they are user-dependent
and require an assignment to the user.
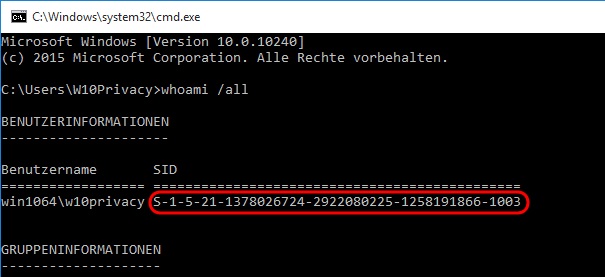
In this case, the user's own user SID (a type of serial number) must be determined beforehand using the "whoami /all" command (this can be found in the fifth line of the output,
see figure below).
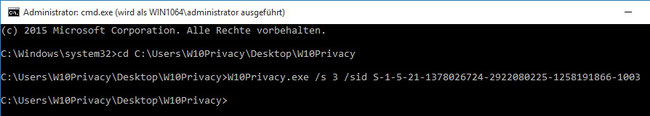
Now the CommandLine command extended by the SID
"W10Privacy.exe /s 3 /sid S-1-5-21-1378026724-292208080225-1258191866-1003"
(the SID specified here, of course, should be replaced by your own SID!) can be used to set the correct network settings for the logged on user.
The changes made during the program run can be verified in the file W10Privacy.log. Alternatively, the program can of course also be started "normally" and the active settings can be
tracked.
Other possible CommandLine parameters are as follows:
"nouserapps" - causes the settings stored in the configuration file to be ignored for the "User Apps" tab. Also, the user apps are not determined, so that the program is
faster.
"nosystemapps" - causes the configuration file to ignore the settings for the "System Apps" tab. Also, the system apps are not determined, so that the program is faster.
"/config Name_of_Ini_File" - this parameter can be used to specify a different configuration file. For example, you could create configuration files for different operating
systems or users and use them by specifying the corresponding configuration file.
Windows updates via W10Privacy
With Windows 10, Microsoft has taken the user's decision on which updates to install, but the updates can no longer be selected individually. At first glance, the user only has the possibility to
install all available updates or none at all.
For the above mentioned reason, many users asked if the selective installation of updates could not be made possible again. In the native Windows 10 interface there are no known ways, but with
some tricks this is possible again via the use of W10Privacyv. 2.0.0.0.
In order to detect, download and install updates via W10Privacy, the "Windows Update PowerShell module" from Microsoft TechNet must first be downloaded and unpacked into the W10Privacy folder.
In W10Privacy you can select and use the option "Windows Updates" under "Extras".
Technical background of the implementation
In order to be able to selectively install updates, first of all a "fake WSUS server" (WSUS servers are usually provided in company networks so that the systems there can obtain the updates locally without having to
have a direct Internet connection) has to be configured for the system through W10Privacy. If this "Fake-WSUS" is configured, Windows cannot download any more updates, because this "Fake-WSUS" does not exist and therefore cannot be reached.
In the course of the search for updates W10Privacy temporarily removes the "Fake-WSUS" and searches for updates via the "Windows Update PowerShell Module" (this works also on systems which do not
have direct internet access and receive internet access via a proxy server -> W10Privacy recognizes a set proxy and uses it for the update search and the download). If updates are found, the
user is shown an overview of the updates in which you can select the updates to be downloaded and installed. After the detection, download and installation of the updates, the "Fake-WSUS" is
reconfigured again and the Windows will not be able to access any other updates.
Important: By setting up the "Fake-WSUS" the system will not receive any updates
without a manual check for updates via W10Privacy! The "Fake-WSUS" can be removed at any time via W10Privacy.
Another hint: Due to the limitations of the tools used in the described mechanics, W10Privacy must not be stored in a path or folder containing spaces for the search for updates!
For example, if you have created a user "Max Mustermann" in Windows and save W10Privacy in a folder "W10Privacy" on the desktop, the path will most likely contain a blank space in the name
(Windows creates the user folders, in which the desktop is located, analogous to the first registered name). In such a case, move the W10Privacy folder to "C: \Temp" and start W10Privacy from
there!
Explanation of the individual settings in the "Windows Updates" menu
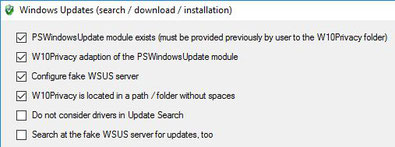
The first setting "PSWindowsUpdate module exists" causes, if the user has downloaded the "Windows Update PowerShell Module" and unpacked it into the W10Privacy folder (the subfolder must be called "PSWindowsUpdate"), that the contents of the "PSWindowsUpdate" folder are stored in the Windows folder "C:\Windows\System32\WindowsPowerShell\v1.0\Modules\PSWindowsUpdate". This is necessary for later use of the PowerShell scripts! If this option is deactivated, the folder "C:\Windows\System32\WindowsPowerShell\v1.0\Modules\PSWindowsUpdate" will be deleted.
The PowerShell scripts of the "Windows Update PowerShell module" need to be slightly customized to be used by W10Privacy. This is done with the second setting "W10Privacy adaption of the PSWindows Update Module". Disabling this option restores the "Windows Update PowerShell module" to its original state.
The third point "Configure fake WSUS- server" is used to enable the "Fake-WSUS-Server" mentioned above. This means that the system is no longer able to check for updates on its
own. Disabling the setting will remove this setting again.
The fourth setting "W10Privacy is located in a path/folder without spaces" simply indicates whether W10Privacy is located in a path/folder without spaces. Activating or
deactivating the setting has no function.
All four of the above settings are prerequisites for checking for updates via W10Privacy. If one of the settings is not set or given, no search is possible.
The setting "Do not consider drivers in Update Search" is optional. This controls within W10Privacy whether drivers are considered in the search for updates or not. It is
important to know that a separate selection of the drivers to be installed is not possible! So either all or none ; -)
The last option "Search at the fake WSUS server for updates, too" is only intended for networks in which a WSUS server is running. By selecting this option, W10Privacy first
looks for updates at the "Fake-WSUS" and then at "Windows Update". A "standard user" should not select this option, the search will take a little longer (it will be searched for at the
"Fake-WSUS" and only after no updates can be detected from there, at "Windows Update").
Notes on the graphic implementation
The graphical implementation of setting the above mentioned settings as well as searching, downloading and installing updates is currently reduced to a
minimum (and therefore more suitable for Windows Power users). If you select the settings you want to change and then click on "Set changed settings", all changes are made in the background (this
may take a few seconds) and after closing the "Windows Updates" window will be displayed updated with the changed settings.
Similarly, although much more detailed information about the process is available when you click on "Start checking for updates". Here the "Windows Updates" window closes and it seems as if
W10Privacy is frozen. Of course, this is not the case! Since dozens of actions take place in the background, not everything can be prepared graphically. If you want to see in
detail the status of W10Privacy, you should download the very useful tool mTAIL and
have a look at the "W10Privacy.log" live. This records all changes: "mTAIL" saves you having to reopen the log file several times in order to keep track of the current status/progress.
If the search is successful, the found updates are listed in a separate window and the desired ones can be selected. Afterwards, the updates are downloaded and installed (you will receive a short
information message in between). With a lot of updates the download and the installation can take quite a long time! Meanwhile, the W10Privacy window is "frozen", no actions can be performed in
it! As mentioned above, a look at the W10Privacy.log (usefully via "mTAIL"!) will help here.
Below is an example of a Windows 10 client showing the updates that are still available for it.
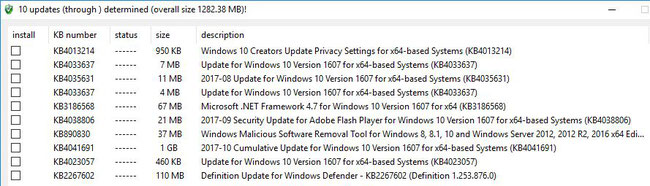
On a Windows 8.1 system that has been idle for some time, a little more updates are displayed.

(c) 2021 by Bernd Schuster
